Welcome 2026: Building Secure and CRA Compliant Fieldbus Systems
As 2025 concludes, we at EmSA (Embedded Systems Academy) would like to thank our clients, partners and suppliers for their trust and cooperation over the past year. We truly appreciate all the projects and shared challenges that you bring to us.
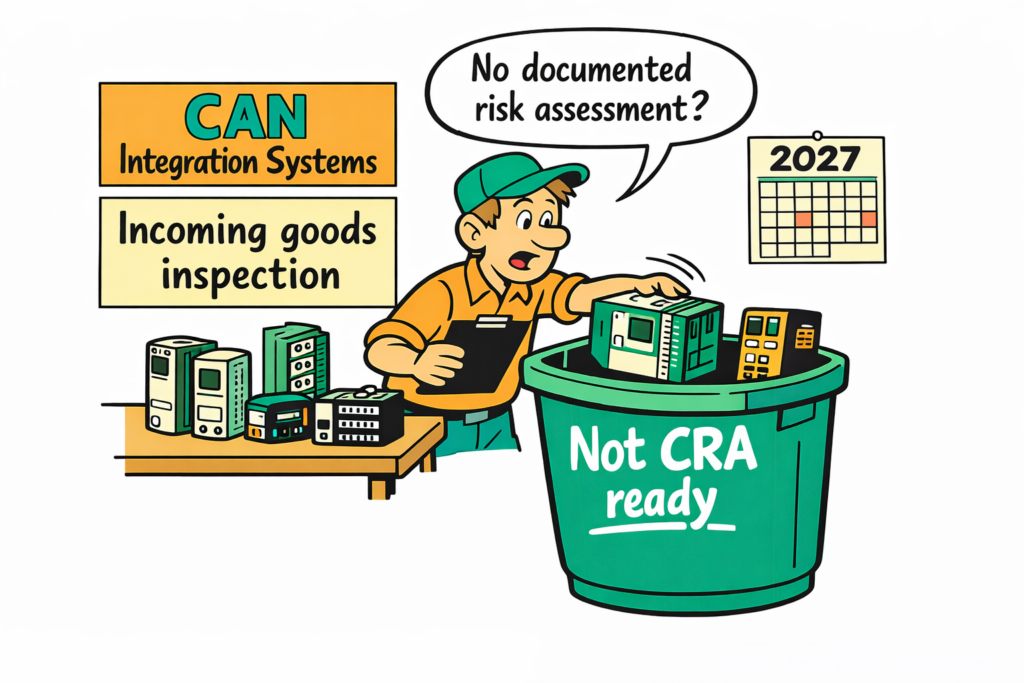
For 2026 our focus will be on fieldbus security and the practical compliance support of the EU Cyber Resilience Act (CRA). By the end of 2027, most of our clients must have their products CRA compliant, this is a huge task, and we are here to help. We already have new CRA training in place to support not only development teams and product managers but also system integrators (emsa.courses). The training is designed for real-world embedded fieldbus products with various downloadable templates and examples.
In 2026 we will also publish our commercial SPsec software solution. SPsec is a security sublayer for small-packet networking technologies and the result of a joint research project with Hochschule Offenburg. It is designed to provide authentication and optional encryption for constrained communication systems such as CAN. The SPsec specification is publicly available in our technical library (SPsec specification).
In addition, we will introduce new hardware CAN modules and interfaces that help to strengthen the security and resilience of CAN-based systems.
Our recommendation to CAN system integrators is simple: Contact your suppliers early about their CRA compliance. Building your CRA compliant product with off-the-shelf CAN components is drastically easier when all suppliers have done their homework and can provide CRA documentation including risk-assessment details. Eventually, system integrators will start rejecting products with below-average or poor CRA documentation.
We look forward to supporting you in making your products more secure and more resilient, ready for the Cyber Resilience Act.
We wish you a successful and innovative year 2026!
 Deutsch
Deutsch English
English




 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD