Is the EU Cyber Resilience Act the end of unprotected, plaintext Fieldbus communication?
The current status of the EU Cyber Resilience Act (CRA) is that manufacturers of devices with digital elements or any software have until 2027 to comply with the outlined rules and regulations. These include compliance issues like overall risk assessment, documentation and incident reporting – which have a huge organizational impact. Technology details mentioned in the CRA are limited, so there is some interpretation as to what it all means for embedded systems and fieldbus communication. When it comes to specifics, the annex talks about how to treat data in transit:
Text excerpts from Annex I, 1. (3) (c) and (d) (emphasis ours):
- Products shall protect the confidentiality of stored, transmitted or otherwise processed data, personal or other, such as by encrypting relevant data at rest or in transit by state of the art mechanisms.
- Products shall protect the integrity of stored, transmitted or otherwise processed data, personal or other, commands, programs and configuration against any manipulation or modification not authorised by the user, as well as report on corruptions.
In other words:
- When communicating or storing (to non-volatile memory) relevant data then encrypt it.
- When communicating or storing (to non-volatile memory) any data then authenticate it.
There is not much room for exceptions here, discussing what is relevant might be challenging. If it is not relevant, then why communicate or store it in the first place?
There might be some relief in Annex I, 1. (1) which says:
- Products shall be designed, developed and produced in such a way that they ensure an appropriate level of cybersecurity based on the risks.
This can be a way out for some applications if in the risk assessment a security expert can show that there is no risk in not protecting certain data. Nevertheless, the security assessment must also reflect the following two statements:
- Apply security-by-design to the entire lifecycle (min 5 years), from development process to production, deployment, and use/maintenance.
- Products integrated in or connected to a larger electronic information system can serve as an attack vector for malicious actors.
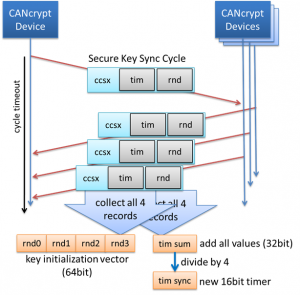
These two statements have a huge impact on all microcontroller communication like plain UART, RS-485, CAN or other fieldbuses. The second statement boils down to not making a difference between important and lesser important communication. Even the lesser important communication may serve as an attack vector to the system.
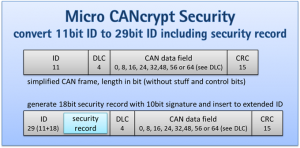
The first statement requires layered security mechanisms given that protecting a single aspect won’t be sufficient. Taking CAN as an example, let us have a look at the known three stages of most common attacks on CAN systems:
- Get access to the CAN communication.
For example by accessing the CAN wires or hijacking a device (or interface to another network) already connected. - Monitor the CAN communication to learn from it.
The attacker learns which CAN frames are used for what. - Inject or replay CAN communication to maliciously trigger behaviour.
The attacker “takes over” certain aspects of the system.
By protecting any one of these three stages, the attacker’s success can be thwarted, and the system might seem “secure”. However, what if in the foreseeable future an attacker finds a way around that single protection? Security-by-design requires that we pay attention to all possible stages of an attack and do not focus on a single point of potential failure.
In any future risk assessment of a system using any form of communication (fieldbus or application specific communications), manufacturers will need to show which steps they took to protect all aspects:
- Which steps were taken to minimize physical access?
How easy is it to access the network wires? Can diagnostic ports be protected? Which interfaces to other networks are there? How are they protected? - Which steps were taken to keep communication confidential?
To prevent attackers from learning anything about the system, encrypt all relevant communication. - Which steps were taken to ensure communication integrity?
To prevent attackers from manipulating frames, authenticate all relevant communication.
In summary, to be EU Cyber Resilience Act compliant, a lot of the future fieldbus communication needs to be both authenticated and encrypted. To simplify the risk assessment and documentation, this should be done for all communication. Otherwise, manufacturers need to be prepared to have a security expert document every unprotected communication as to why this specific data set is irrelevant enough so that even if read or manipulated it won’t possibly constitute a cybersecurity risk.
Follow this blog and/or our LinkedIn page to learn about latest related developments including our upcoming security solutions for CAN, CAN FD, CANopen and CANopen FD.
 Deutsch
Deutsch English
English






 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD