The 15th international CAN Conference took place in Vienna on October 27th and 28th 2015. On two days, a total of 23 papers were presented. Topics included current application examples, security and IoT (Internet of Things) issues and “everything” CAN FD (Flexible Data Rate) related. CAN FD with its increased data rate was the major topic of this conference, many papers were directly related to it.
As CAN FD is not backward compatible to CAN, one of the session topics was migration from CAN to CAN FD. Mixing CAN and CAN FD controllers is only possible if the CAN FD messages are hidden from the CAN controllers as they would generate error frames upon reception. One approach is using partial networking transceivers where traditional CAN controllers are put to sleep during CAN FD communication. After seeing a specific sleep message, transceivers for partial networking can keep the connected CAN controller in sleep mode until a specific wake up message is received – no other message on the network causes a wake-up.
NXP presented a paper about their “FD Shield” transceiver. This transceiver is used to connect legacy CAN controllers to a CAN FD network. The CAN FD traffic is somewhat “shielded” from the CAN controller, only regular CAN traffic passes through but CAN FD messages are blocked as soon as they can be detected. However, there is a side effect: Each CAN FD frame on the network causes a local, not propagated receive error at the CAN controller side. As a result the CAN controller may go error passive. However, as transmits works fine, it will not go bus off and can still be used. Although not perfect, this is a quick and easy solution during a migration phase from CAN to CAN FD.
Another way to quickly connect to CAN FD networks is using Microchips external CAN FD controller using an SPI connection to the host controller. Here designers need to carefully choose the clock rate used on the serial interface side; depending on the CAN FD data rate used the SPI clock might need to be 10 or even 16Mhz. If a CAN FD data rate of 8Mbps is used, then a 10Mhz clock rate on the SPI side is sufficient to handle 100% bus load. However, the host controller of course needs to be able to handle the 10Mhz SPI traffic, too.
Other papers showed how CAN FD can be used in Linux systems, AUTOSAR and J1939, In general, the physical layout for CAN FD networks is not as flexible as it is with regular CAN. With faster bit rates ringing and reflections become more of a problem as they used to be. As usual, if an application tries to get close to the physical limits that a technology provides, more care must be taken when determining the physical layout and terminations.
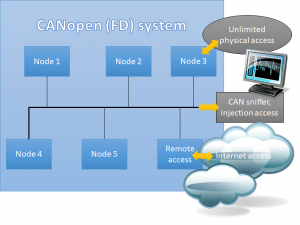
With more and more CAN networks also getting some “remote access” option or even a gateway/firewall to the Internet, security of CAN networks suddenly becomes more important. In the past, CAN networks could be regarded as “closed” (inside a machinery, no remote access) so no precautions were taken in regards to security. Once a CAN network goes “online”, even if it is by the means of some firewall and even if it is only part-time, the entire security concept needs to be re-evaluated. Recent car hacks have shown that once hackers are past the firewall, they can do “anything” because there is no security layer in the CAN network.
Papers from Robert Bosch GmbH and the CiA showed some possible options to add encryption also to CAN communication, however, that directly has an impact on debugging and testing. If communication between two ECUs is secure, how do we monitor or debug it? So the debugger/tester/logger needs to part of this equation, too. It will be interesting to see where this goes, will at some point security be added to all CAN communication or will it be limit to “relevant” transmissions like commands that actually do something to the system?
Once the papers are added to the CiA’s server system, they will be available for download.

 Deutsch
Deutsch English
English


 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD