A summary of the technical features used by CANcrypt
By Olaf Pfeiffer, Embedded Systems Academy GmbH, 26th of February 2016
At the Embedded World 2016 in Nuremberg, Embedded Systems Academy GmbH announced their book “Implementing Scalable CAN Security with CANcrypt”. The corresponding CANcrypt demo code will be published using an open license. At the Embedded World we have seen a lot of interest in the technical details. For those who do not want to wait until the publication of the book this article summarizes the key technical features of CANcrypt (also see our CANcrypt.eu web page for more information).
Core Functionality of CANcrypt
CANcrypt provides the following services:
- Pairing: dynamic generation of a random key that is only known by the paired devices; optionally, one device can enforce a preset key to the other.
- generate and exchange keys
- optional storing of keys in non-volatile memory for permanent pairing
- support of a key hierarchy when multiple keys are stored
- maintain dynamically changing key (pseudo one-time pad)
- dynamic key updated using shared random bit
- Grouping: multiple devices share a common dynamic key
- originally assigned through pairing
- maintain dynamically changing key (pseudo one-time pad)
- dynamic key cyclically updated by all grouped devices
- Safety communication: any secure communication uses a preamble message
- messages received are only accepted and passed on to application if together with the preamble the authentication and decryption is verified successfully
- preamble identifies message CAN ID, security features used, has a counter and a signature
- secure messages must be received within 10ms after the preamble to be valid
CAN message IDs required:
- one CAN ID for each participating device
- used for preamble and control messages
- a CAN ID pair used for the random bit generation cycle
Cipher methods used
CANcrypt keys are symmetrical and dynamic, they are continuously updated. From the dynamic key and a message counter a pseudo one-time pad is generated that is used for the simple, customizable encryption.
If the secure pairing is only active for two nodes, a random bit generation cycle is used continuously in the background to introduce new bits to the dynamic key. If multiple nodes are paired, then the dynamic key update information is sent via an encrypted message.
The system pairing process is started using a CANcrypt configurator device. This can be done by a system builder or integrator once the CAN system is installed. It must happen in a secure environment. The keys generated at that time are stored locally in the devices connected – there is no need to keep any further copy of this key outside the system, minimizing the effort placed on key management. The keys cannot be duplicated. If a new device is added (or one exchanged), all keys need to be erased and newly generated.
As stored keys in each device make up a hierarchy, we can guarantee that erasing and regenerating keys can only happen when the configurator used is logged-in to the system based on a key high enough in the hierarchy to allow erasing and re-paring.
Operating principle for random bit generation
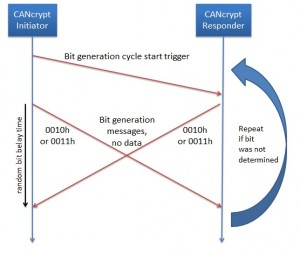
Bit generation cycle
Solely by monitoring CAN messages, one cannot identify the device that sent any individual message, because at that level, any device can transmit any message. As an example, let us allow two devices (named initiator and responder) to transmit messages with the CAN IDs 0010h and 0011h (and data length zero) within a “bit select time window”. Each node shall then randomly choose and send one of the two messages at a random time within the time window.
At the end of the bit select time window, a trace recording will show one of the following scenarios:
- One or two messages of CAN ID 0010h
- One each of CAN ID 0010h and 0011h
- One or two messages of CAN ID 0011h
Let us have a closer look at case 2 – one each. If these are transmitted randomly within the bit response time window, then an observer has no way to identify which device sent which message. However, the devices themselves know it and use this information to derive a bit from it.
Unfortunately we cannot use case 1 and 3, so if those happen, both nodes need to recognize it and re-try, using another next bit select time window.
Note 1: If one device wants to enforce a specific bit to the other, it may generate a “flip bit” message at the end of the cycle to indicate to the other device that this bit needs to be flipped.
Note 2: A variation of this scheme is to not use a random delay, but instead ensure that both devices transmit their message immediately after the trigger message. Then both messages arbitrate the bus at the same time and in a trace recording we will always see 0010h followed by 0011h.
Potential attacks: As usual, a denial-of-service kind of attack is always possible. By injecting messages an attacker can break the cycle, the devices would not be able to exchange a key in the first place. If an attacker has full physical access (oscilloscope, transceiver), he can determine which node sent which message. However, there is still some effort required to recognize which bits were actually generated (as participating devices can change interpretation). Last but not least anything “random” is always an attack vector. The participating devices need a reasonably good random number generator.
 Deutsch
Deutsch English
English

 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD