February 24, 2020 – Embedded Systems Academy (EmSA) and NXP® Semiconductors announce the integration of the free-to-use EmSA Micro CANopen libraries into the NXP MCUXpresso Software Development Kit (SDK) for developing with NXP’s microcontrollers (MCU) and crossovers based on Arm® Cortex®-M.
For years, many MCUs have been equipped with the Controller Area Network (CAN) interfaces including CAN FD. These interfaces are optimized for embedded communication and make it easy to transmit and receive single messages.
“To take full advantage of the capabilities of such interfaces, middleware communication protocols are required,” says Olaf Pfeiffer, General Manager of EmSA. “One of the most
popular protocols for embedded CAN applications is CANopen, for which EmSA has delivered its Micro CANopen software for more than 20 years, and remains highly used among embedded developers.”

Free-to-use versions of EmSA’s Micro CANopen library are now fully integrated into the MCUXpresso SDK for a selection of NXP LPC MCUs and i.MX RT crossover MCUs.
“This integration further simplifies the process of prototyping and integrating sophisticated and reliable communication into embedded systems.” said Brendon Slade, director of MCU ecosystem for Edge Processing at NXP Semiconductors. “For most systems, the libraries can be used in production without further licensing.”
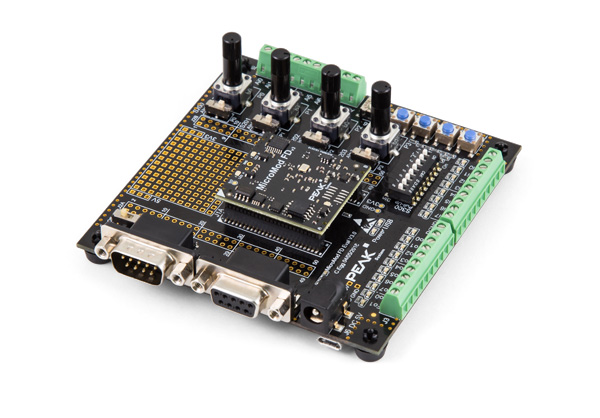
One of the first adopters is PEAK-System Technik: Their industrial I/O module PCAN-MicroMod FD is based on NXP’s LPC54000 MCU series and uses a variation o
f EmSA’s Micro CANopen libraries. “Using a proven CANopen (FD) protocol implementation for our I/O devices greatly reduced our development time and opens up additional use-cases for our customers.”, says Uwe Wilhelm, General Manager of PEAK-System Technik.
For more information about the NXP microcontrollers currently supported by EmSA’s free to use CANopen libraries and video tutorials, visit www.em-sa.com/nxp
About MCUXpresso SDK
Available in downloads based on user selections of MCU, evaluation board and optional software components, the MCUXpresso SDK merges customization and quality in a suite of production-grade runtime software. Complete with pre-integrated RTOS middleware, stacks and middleware, reference software, and MISRA-compliant drivers analyzed with Coverity® static analysis tools, it’s the ultimate software framework and reference solution for application development with NXP MCUs and crossover MCUs based on ARM® Cortex®-M cores.
About Embedded Systems Academy
Embedded Systems Academy (EmSA) is an NXP gold partner and has locations in Barsinghausen, Germany and San Jose, California. EmSA provides tools, training and services for planning, implementing, debugging, commissioning and testing of embedded networking technologies including CAN, CAN FD, CANopen, CANopen FD, CiA447, J1939 and others. EmSA’s tutors Olaf Pfeiffer, Christian Keydel and Andrew Ayre published two books about CAN, CANopen and security on CAN systems. They regularly publish related articles and papers for various international conferences.
Contact
Embedded Systems Academy GmbH
Olaf Pfeiffer
info@esacademy.de
 Deutsch
Deutsch English
English



 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
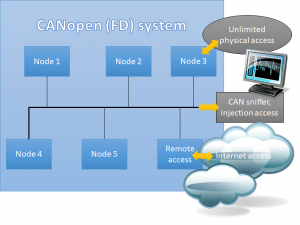
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD