See you at the upcoming shows and conferences: #EW2020 and #iCC2020
This year we present multiple papers at the upcoming Embedded World (25th to 27th of February in Nuremberg, Germany) and the international CAN Conference (17th to 18th March in Baden-Baden, Germany). Chris and I will be talking with our partners of NXP Semiconductors, PEAK
-Systemtechnik and the Hochschule Offenburg about CAN (FD) security and CANopen (FD) Smart Bridging. In our security papers, we examine how different existing and CAN capable security methods can best complement each other. With SmartBridgingFD we show how classical CANopen devices or networks can easily and transparently be mixed with newer CANopen FD installations. As classical CANopen and CANopen FD are not compatible on the bitrate level, they can not share the same CAN wiring. However, the SmartBridgeFD allows combining classical CANopen and new CANopen FD networks into one large logical network.

At the Embedded World, you can see the SmartBridgeFD integrated into the CANopen FD demonstrator at the CiA booth (hall 1 booth 630). Another of our CANopen (FD) demos will be displayed at NXP Semiconductors (hall 4A booth 220), as our CANopen software is now part of NXP’s latest SDK. Our CAN hardware partner PEAK Systemtechnik is in hall 1 (booth 483).
The Embedded World conference program is now online, we are in Session 2.1. The program for the international CAN Conference is here, our papers are in Session IV and VII.
 Deutsch
Deutsch English
English




 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
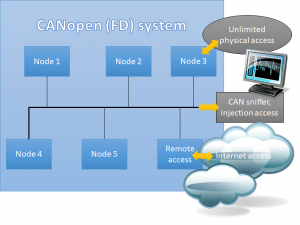
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD