CAN (FD) / CANopen (FD) security specification updates
![]() Our authors Christian Keydel and Olaf Pfeiffer published an article in the current CAN newsletter, summarizing the current status of CAN security specifications.
Our authors Christian Keydel and Olaf Pfeiffer published an article in the current CAN newsletter, summarizing the current status of CAN security specifications.
Please follow the link above for more details.
Excerpt:
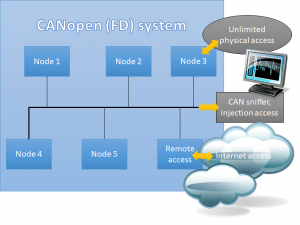
End of June 2019, the CiA association hold a phone conference for safety and security issues. Holger Zeltwanger gave the participants an update regarding “base documents”. When defining security solutions for Classical CAN, CAN FD, or CAN XL systems, it would be preferable to not start from scratch defining security basics for embedded systems or embedded communication systems. Unfortunately, the current draft of ISO 21434 “Road Vehicles – Cybersecurity engineering” does not seem to be suitable, as it is very generic and not yet completed. It is more of a guideline what designers and developers need to keep in mind when designing a “secured” vehicle.
Another document suggested is the “Baseline Security Recommendations for IoT” by the European Union Agency for Cybersecurity. Until the next meeting, CiA will review and report, if that document is suitable to be referred to also by CiA documents. CAN XL is still in an early specification phase and the related special interest group, recognizing the possibility for security features in hardware to be part of future CAN XL controllers, therefore suggested adding security features to CAN XL first. One of the discussed options is a blacklist/whitelist scheme like the one implemented by the NXP secure CAN transceiver family. Such a scheme can eliminate several potential attack vectors at once if all participants in a CAN (XL) network actively support it. Once we see which security features made it into the CAN XL specification (and hardware), we can review if any of these can still be applied to CAN FD, too, for example on the transceiver level.
However, potential CAN controller specific hardware security features will most likely not be suitable to migrate back into CAN FD, so protocol based security solutions are still required.
 Deutsch
Deutsch English
English




 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD