Two-year project for security of CANopen and other small-packet networks
Together with the Institute of Reliable Embedded Systems and Communication Electronics (ivESK, Prof. Sikora of Offenburg University), the Embedded Systems Academy has been awarded a research grant for a collaborative project focusing on embedded network security. The project is dedicated to developing a security framework for small-packet networks, with a specific emphasis on CAN and CANopen systems.
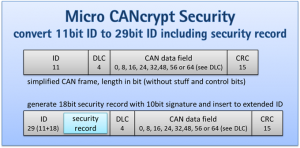
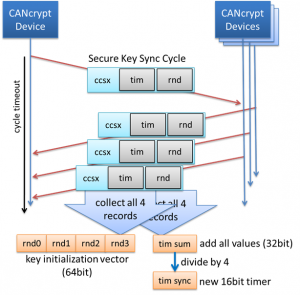
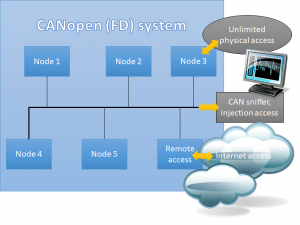
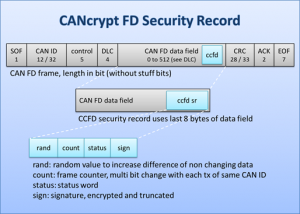
The initiative, internally referred to as “Inter-Layer Multi-Participant Security for Small-Packet Networks,” can be integrated within existing network layer protocols and offers multi-party security. It is adaptable to various small-packet network protocols used in embedded systems. Beyond CAN, CAN FD, CANopen and CANopen FD, it can also be used for I2C or RS-485 based systems. The project aims to combine established security mechanisms in a novel way and adapt them suitable for deeply embedded systems, devices and networks, where resources, such as memory, computing power, data rates and frame length are very much constraint.
The project’s goal is to ensure that the results are openly available and can be reused by the Special Interest Group “Safety/Security” within CiA (CAN in Automation).
We plan to regularly publish updates on our project’s progress. A first presentation is scheduled for the embedded world Conference in Nuremberg: On April 9th, 2024, we will present the paper “Collaborative Design of Security Measures for CAN and CANopen Systems” in the connectivity track, session 2.2 on CAN. If you are interested in contributing to the specification process or in beta-testing early implementations, please feel free to contact us (contact form on this web page or mail to info@esacademy.de).

This Project is supported by the Federal Ministry for Economic Affairs and Climate Action (BMWK) on the basis of a decision by the German Bundestag.
 Deutsch
Deutsch English
English






 Learn about our current product range for embedded systems
Learn about our current product range for embedded systems


 Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices.
Embedded Networking with CAN and CANopen. Your technology guide for implementing CANopen devices. Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD
Implementing scalable CAN security. Authentication and encryption for higher layer protocols, CAN and CAN-FD